In the era of global digital communication, how to provide convenient service experience while ensuring security and compliance has become an important issue for cloud communication platforms. IntBell skillfully balances the dual needs of security protection and user experience through an innovative hierarchical real-name authentication mechanism. This article will comprehensively analyze the design concept, implementation details of IntBell’s real-name authentication system and its actual value to users, so as to provide more powerful communication capabilities for compliant users.
Hierarchical Authentication System: Unlocking Step-by-Step Communication Capabilities
1. Scientific Design of SMS Sending Quota
IntBell adopts a progressive permission granting model. Through the positive correlation between authentication level and communication capabilities, it not only prevents abuse but also rewards compliant users:
| Authentication Level |
Daily SMS Limit |
Applicable Scenarios |
Review Timeframe |
| Unauthenticated |
5 messages |
Testing experience |
Instant |
| Basic Authentication |
50 messages |
Personal basic communication |
1-2 working days |
| Advanced Authentication |
300 messages |
Operation of small and micro enterprises |
1-2 working days |
2. Typical Application Scenarios for Each Level
- Unauthenticated status: Suitable for new users to experience functions and use in test environments
- Basic Authentication: Meets regular needs such as cross-border e-commerce order notifications and logistics updates
- Advanced Authentication: Supports high-intensity communication scenarios such as marketing activities and member services
Data comparison: The average customer reach efficiency of enterprise users who have completed advanced authentication has increased by 3 times, which proves that this mechanism effectively distinguishes legitimate business needs from abusive behaviors.

Analysis of the Entire User Authentication Process
1. Authentication Entrance and Path Navigation
Users can complete authentication upgrade through the following steps:
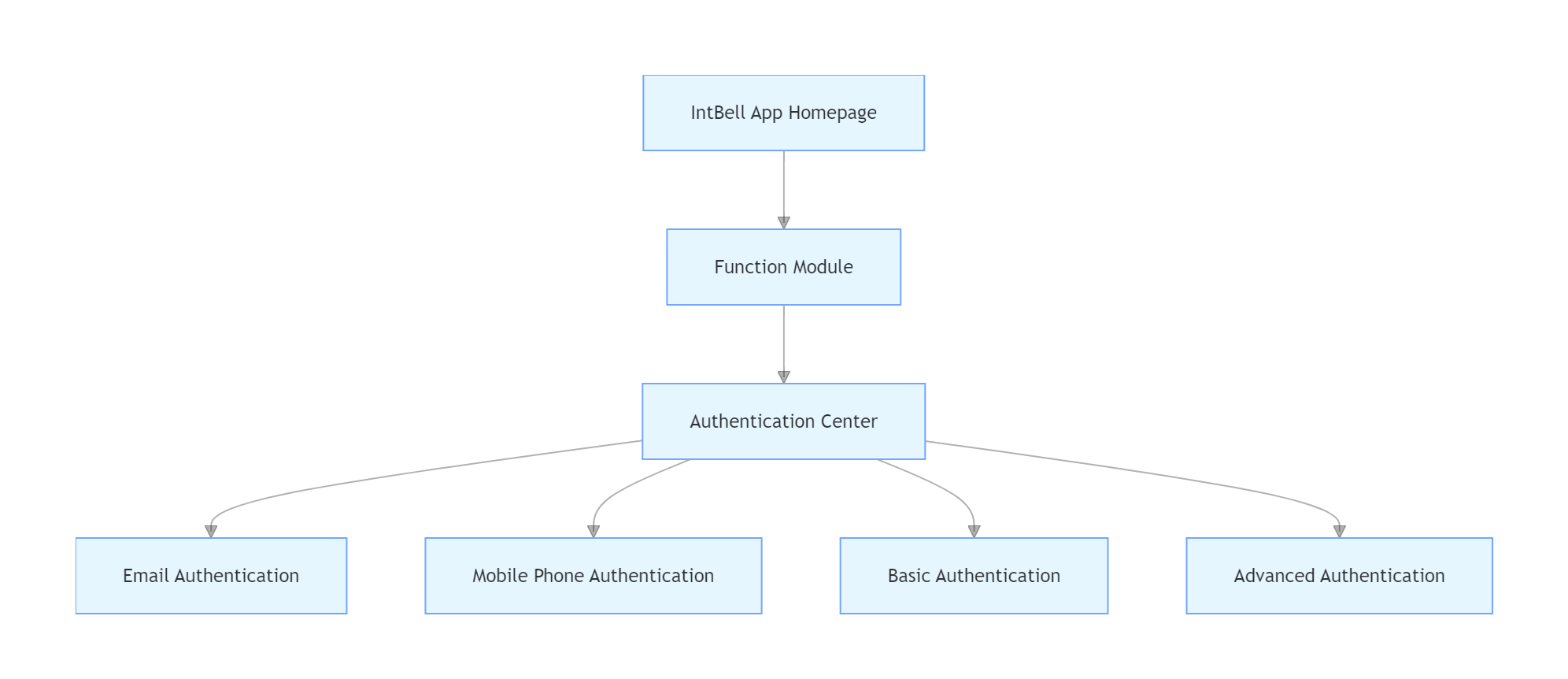
2. Specific Requirements for Each Stage of Authentication
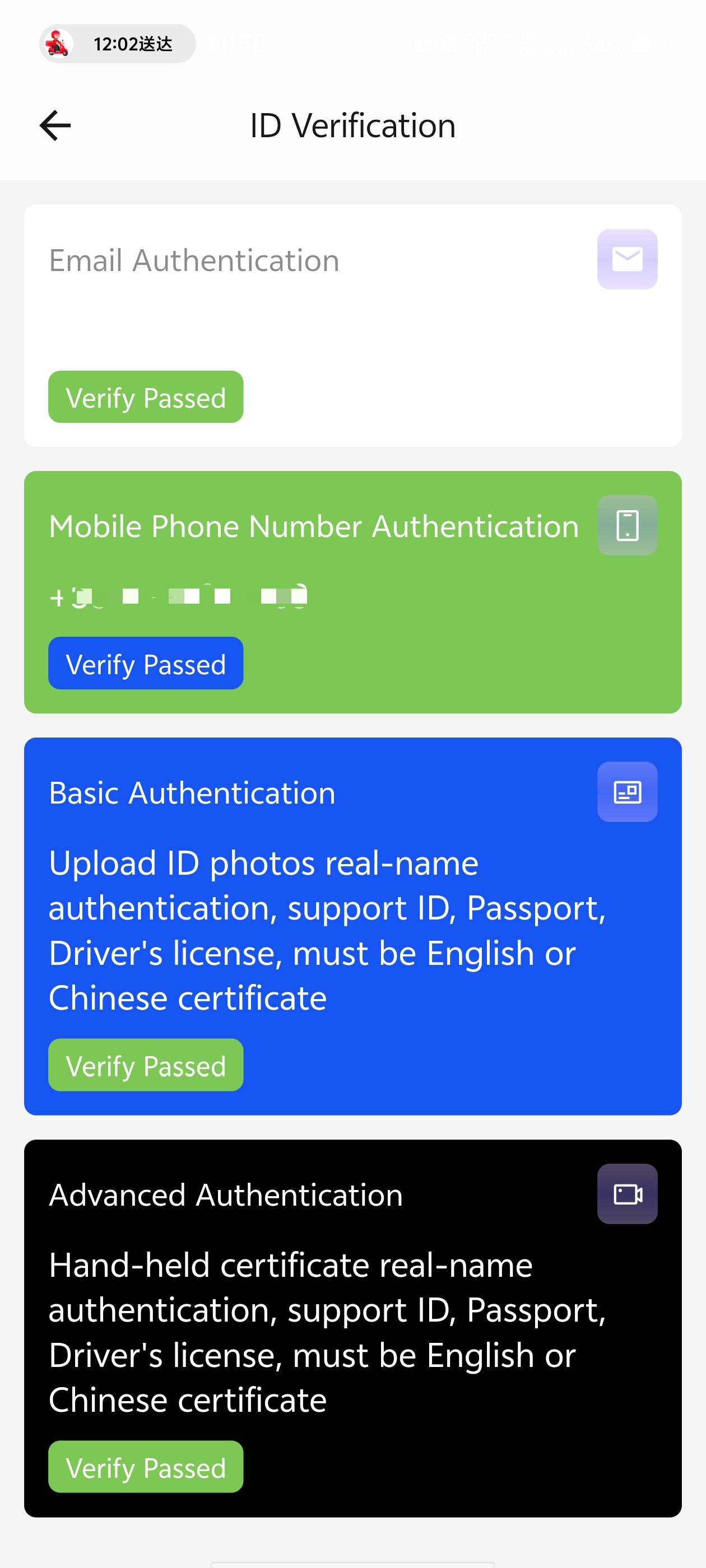
Email/Mobile Phone Authentication
- Verification method: Verification by receiving a verification code
- Required materials: None
- Review time: Takes effect immediately
- Security reminder: It is recommended to bind the corporate email and administrator’s mobile phone number
Basic Authentication (Document Verification)
- Supported documents:
- ID card: Residents of Chinese mainland, Hong Kong, Macao and Taiwan
- Passport: Universal in multiple countries
- Driver’s license: Universal in multiple countries
- Document requirements:
- Clear photos
- Size not exceeding 5MB
- Only Chinese or English documents are accepted
- Review points:
- Verification of document authenticity
- Basic information is clearly identifiable
- Not expired
Advanced Authentication (Biometric Verification)
- Additional requirements:
- Half-body photo holding the document
- Real-time liveness detection
- Document and face matching verification
- Shooting guidelines:
- Sufficient light, no遮挡 on the face
- Document information is clearly visible
- Simple and unmodified background
- Security protection:
- Adopting blockchain deposit technology
- Automatically blur sensitive information
- Encrypted storage of biometric features
3. Authentication Status Management
- Progress inquiry: The authentication center displays the review status in real-time
- Validity period: Only one authentication is required to pass
- Appeal channels: Provide dual channels of online customer service and email appeal
Note: Only the main account needs to be authenticated for real-name authentication, and sub-accounts do not need to be authenticated
User Value and Implementation Suggestions of the Authentication Mechanism
1. Authentication Strategies for Different Types of Users
| User Type |
Recommended Level |
Authentication Value |
Implementation Tips |
| Individual developers |
Basic Authentication |
Unlock API testing permissions |
Prioritize passport authentication |
| Cross-border e-commerce |
Advanced Authentication |
Ensure large-volume SMS sending |
Prepare required documents for authentication in advance |
| International logistics |
Advanced Authentication |
Ensure large-volume SMS sending |
Prepare required documents for authentication in advance |
| Startups |
Basic Authentication |
Control initial costs |
Gradually upgrade as the business grows |
2. Solutions to Common Problems
Problem: Documents are not in Chinese or English
Solution: Provide certified translations + original documents
Problem: Review is rejected
Solution: Check whether the corners of the document are complete and whether reflections affect information recognition
Problem: Urgently need to increase the quota
Solution: Contact customer service for expedited processing
3. Best Practice Case
Case background: A cross-border maternal and infant e-commerce company faces the following challenges:
- Unauthenticated status limits business expansion
- Concerns about privacy risks in the authentication process
- Demand for unified management of multinational teams
IntBell solution:
- Phased authentication:
- First week: Complete basic authentication
- Second month: Upgrade to advanced authentication
- Privacy protection measures:
- Use passport instead of ID card for authentication
- Enable unified management of corporate accounts
- Efficiency improvement:
- SMS quota from 50 to 300 messages/day
- Customer notification delivery rate increased to 99%
Implementation results:
- International orders increased by 220% within 6 months
- Zero privacy-related complaints
Conclusion: Synergistic Progress of Security and Development
For users, completing authentication is not only a necessary step to meet compliance requirements but also a key to unlocking business growth potential. As IntBell continues to optimize the authentication process, it will further simplify the verification steps for honest users on the premise of ensuring security in the future, realizing a true “one authentication, global smooth communication”.
In an era where digital trust has become a scarce resource, choosing IntBell means choosing a communication platform that is both safe, reliable and full of development opportunities. Download the app to complete authentication upgrade immediately, and let your international business move forward at full speed on the track of compliance!





